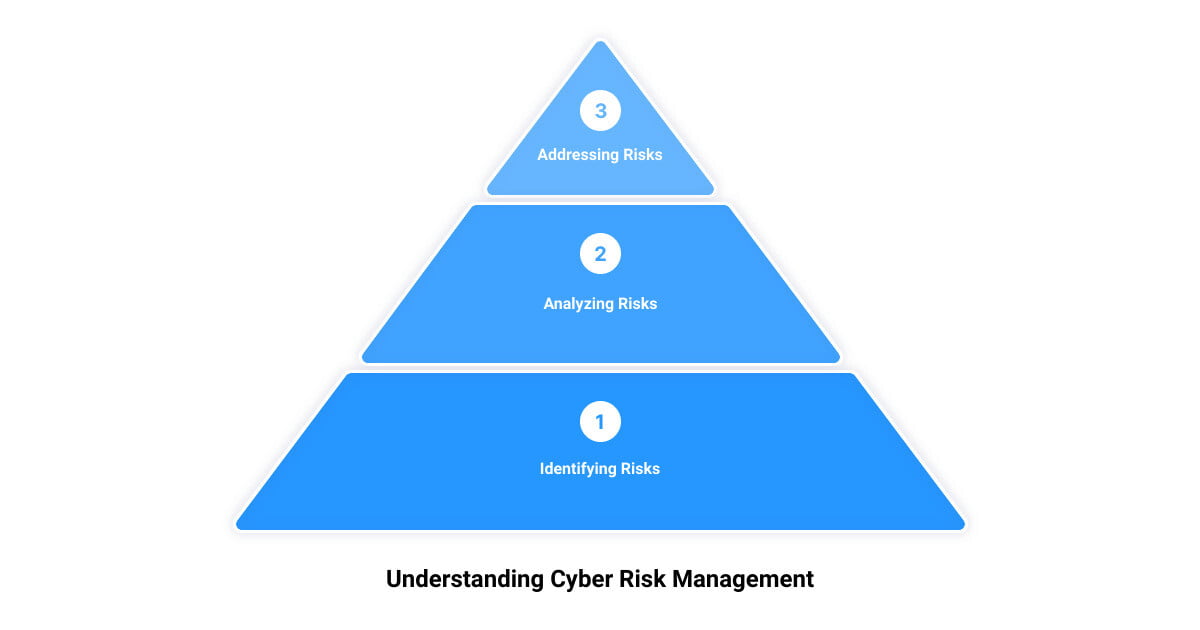
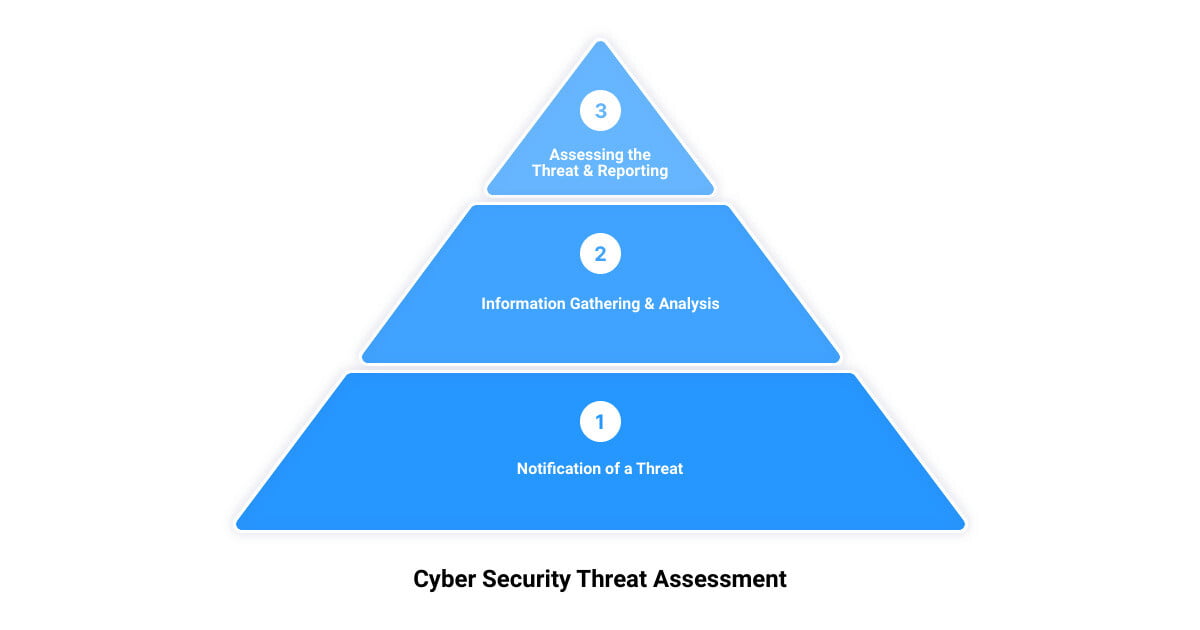
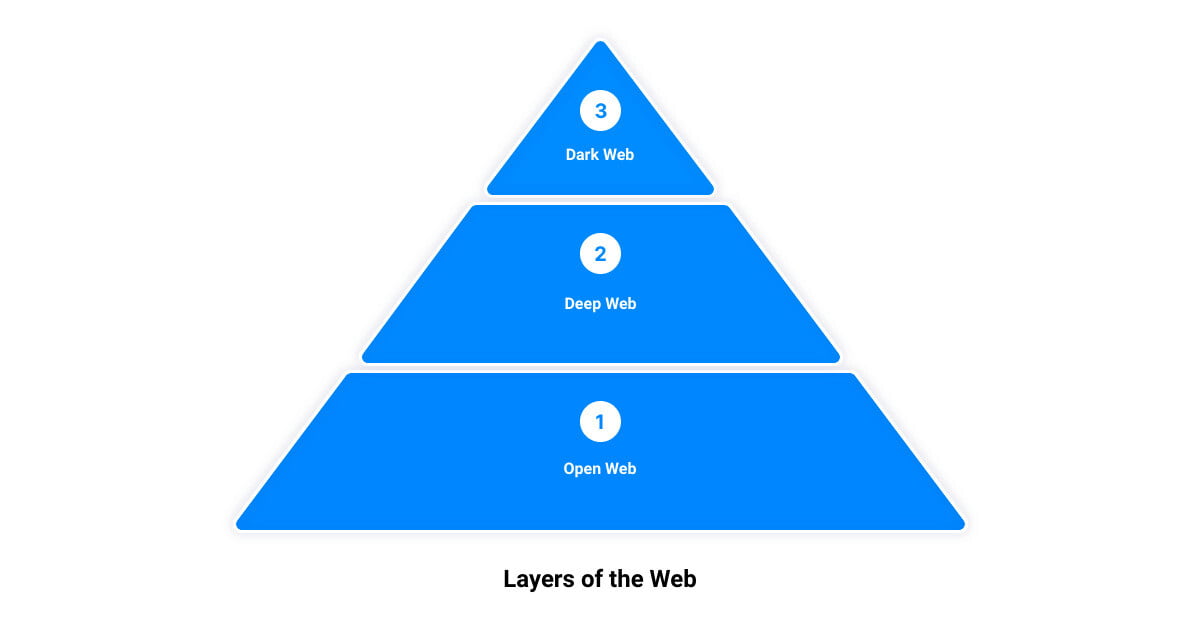
Unmasking Cyber Threats: The Art of Uncovering Hidden Vulnerabilities
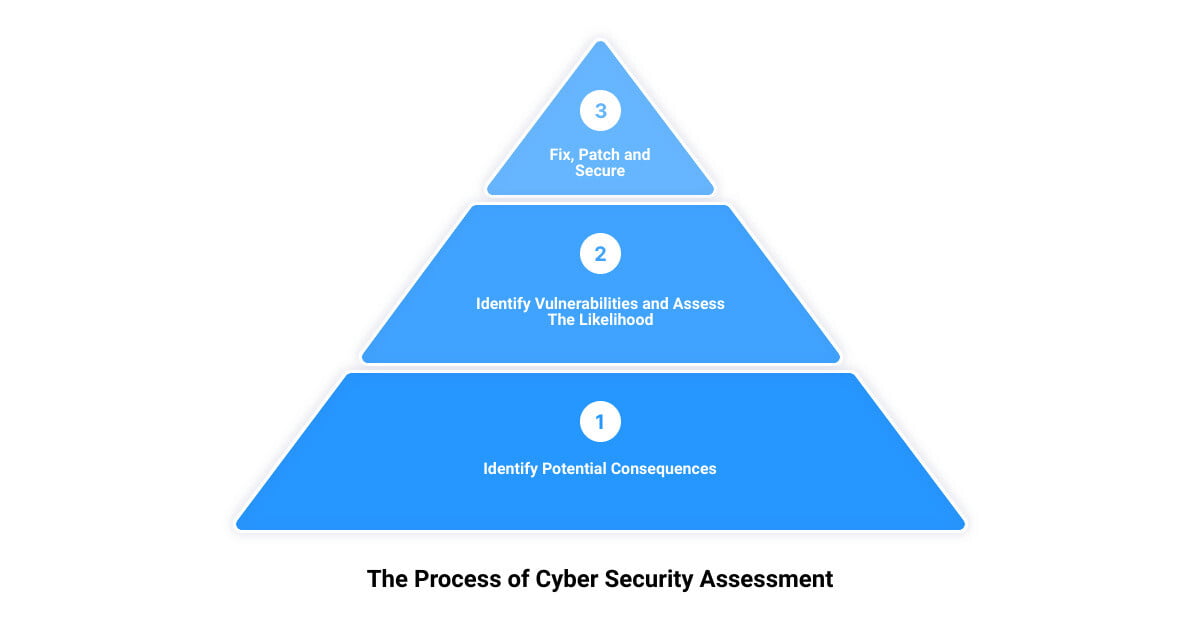
Introduction: The Importance of Vulnerability Assessment in Cyber Security In the modern digital landscape where businesses are increasingly dependent on technology, cyber threats pose a significant risk. To stay ahead…